Search for "Andi" returned 7404 results

26 min
ChokePointProject - Quis custodiet ipsos custodes?
Aggregating and Visualizing (lack of) Transparancy Data in…

52 min
3G Investigations
Scanning your GPRS/UMTS IP network for fun and profit

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…
69 min
DG103: Wikidata
Dive into the free knowledge base and build things with it!

39 min
Digital dissent in Latin America
How the Internet is impacting organizing and dissent in…

43 min
How we changed openSUSE developement
Going from generic distro to stable rolling and feature…
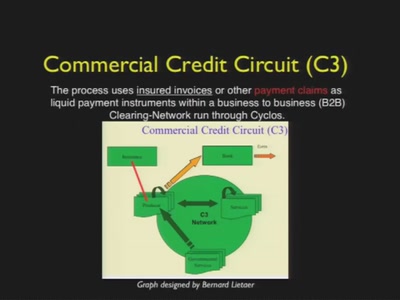
77 min
Imagine the Future of Money
Economic transformations, hacker culture and why we should…

93 min
Bluetooth Hacking - The State of The Art
A roundup and live demonstrations of all currently known…

56 min
Biohacking in art
An interdisciplinary foray from slime moulds to fungi and…

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…
51 min
Open Source in the WSN Research
Experiences made with free and open source software in…

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…
20 min
The Nibbletronic
A DIY MIDI Controller and a New UI for Wind Instruments

53 min
Privaterra - Report from the field
IT Security and Human Rights organizations - The needs, the…
68 min
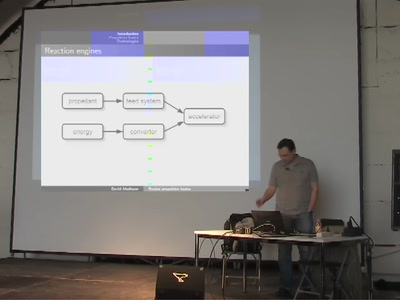
Rocket propulsion basics
An introduction to rocket engines and their application for…

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

50 min
Data Analysis in Terabit Ethernet Traffic
Solutions for monitoring and lawful interception within a…
24 min
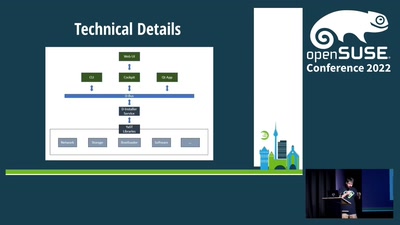
D-Installer Project: Carving a Modern Installer
A new installer based on D-Bus, YaST, Cockpit and web…
30 min
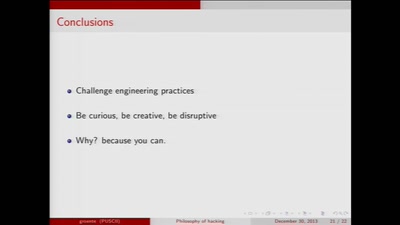
The philosophy of hacking
Contemplations on the essence of hacking and its…

71 min
Security in the cardholder data processing?!
Experiences and lessons learned with the Payment Card…
51 min
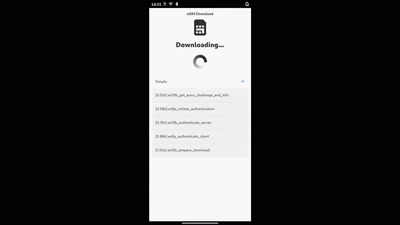
eSIM management on Qualcomm phones
Using an open-source and mainline Linux stack to work with…
32 min
(Virtual Talk) GitOps meets dotfiles: Never Setup a New Machine Again!
Running your Window Manager and Applications in non-root…

61 min
Human body as an electric IO system
Hacking your brain, and other body parts. Debunking myths…
33 min