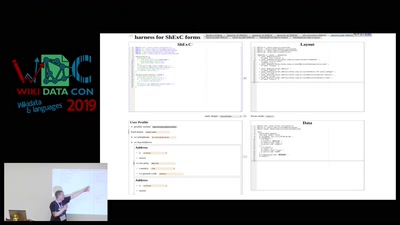
Search for "ari" returned 5235 results
40 min
The Joy of Intellectual Vampirism
Mindfucking with Shared Information
39 min
Integrating Uyuni with Ansible and Terraform
...and even more?

49 min
Godot meets JetBrains:
Building IDE tools for a growing engine

61 min
Hackers As A High-Risk Population
Harm Reduction Methodology

47 min
Public Domain
Ein Plädoyer für die Lizensierung freier Inhalte als…
61 min