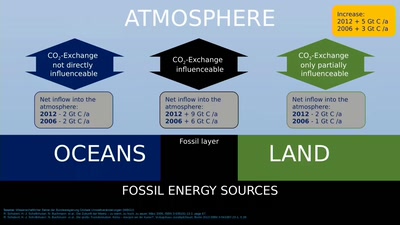
Search for "Kay" returned 3826 results
28 min
Accelerating Scientific Research through Spinning Out a Software Company
Our story about finding the balance between free and…
22 min
Putting Players First
Human-Centered Game Development towards Accessibility &…

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

38 min
IT-Sicherheit für Verbraucher stärken
Entwicklung eines IT-Sicherheitsbewertungssystems für…

95 min
Platform System Interface
Design und Evaluation holistischer Computerarchitektur

41 min