Search for "Seth Hardy" returned 899 results

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild

60 min
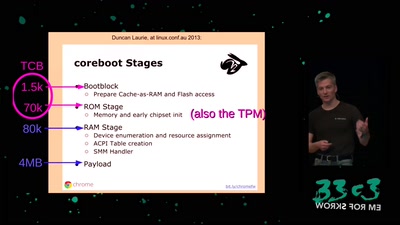
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…

34 min
Scuttlebutt
The decentralized P2P gossip protocol

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie
43 min
Seeds of Change
Unlearning & Radical Collective Change in Online Communities

29 min
What de.fac2?
Attacking an opensource U2F device in 30 minutes or less

33 min
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley

58 min