Search for "Kay" returned 3826 results

61 min
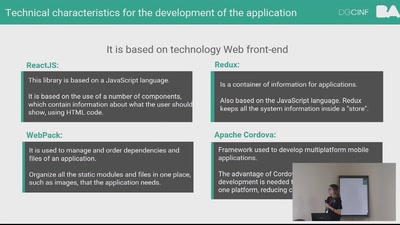
DevOps but for artworks in museums
A look into pipelines ending in museums and not in the cloud

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks
38 min
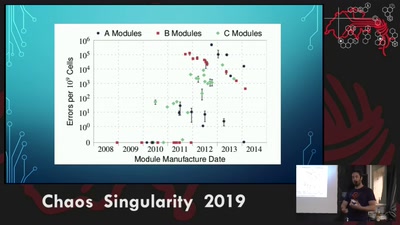
Rowhammer exploit
Viability of the Rowhammer Attack when ECC memory is used

26 min
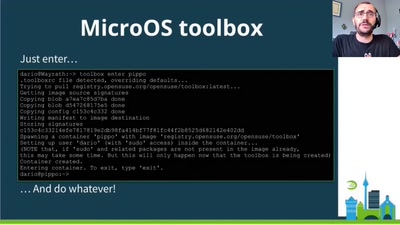
Don't scan, just ask
A new approach of identifying vulnerable web applications
35 min