Search for "Ann" returned 10887 results

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

21 min
Closing Event
Good Bye and have a safe trip home!

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society
60 min
Resisting Surveillance: it's is not just about the metadata
The infiltration and physical surveillance of social…
![for women in "${tech[@]}"; do](https://static.media.ccc.de/media/conferences/camp2015/6774-hd.jpg)
26 min
for women in "${tech[@]}"; do
Let's talk, share and learn from each other.
58 min
Advanced memory forensics: The Cold Boot Attacks
Recovering keys and other secrets after power off

38 min
Honey, let's hack the kitchen:
Attacks on critical and not-so-critical cyber physical…

44 min
ASLR on the line
Practical cache attacks on the MMU

42 min
Neoliberalism has been killing us - Chile is awakening
The Chilean peoples´struggle for dignity and social equality
32 min
Cryptokids
empower kids and provide tools for them to be more secure…

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…

28 min
Behind the scenes of the OBS team
Tools, processes and procedures used by the OBS team
32 min
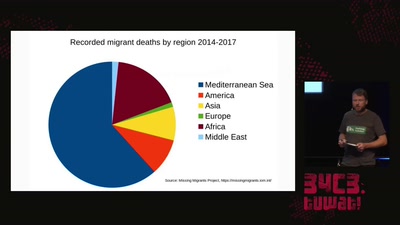
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

57 min
The Age of Literate Machines
A Visionary Look at Free Software and Open Source
49 min
Future 3.0
One Theory on Patterns in Culture, Technology and Commerce
28 min
Solar-powering your Geek Gear
Alternative and mobile power for all your little toys
41 min
Hacking on the Nanoscale
Dual Beam Devices for Rapid Prototyping and Reverse…

61 min
The A5 Cracking Project
Practical attacks on GSM using GNU Radio and FPGAs

63 min
What's the catch?
Funding open source with money from corporations and…

40 min
Crypto Dawn
A To Do list for Cyptographic Research and Implementations

60 min
Internet Cube
Let's Build together a Free, Neutral and Decentralized…
35 min