Search for "Jong-Hoon Lee" returned 553 results
35 min
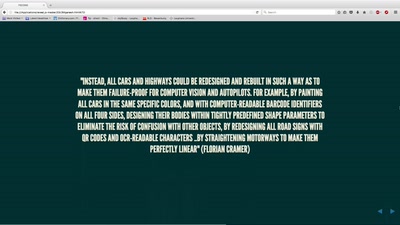
Ethics in the data society
Power and politics in the development of the driverless car

60 min
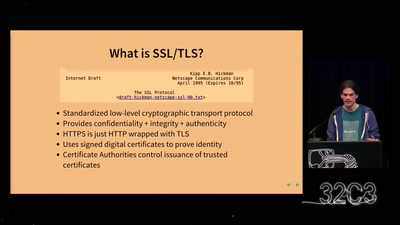
Beyond your cable modem
How not to do DOCSIS networks
21 min
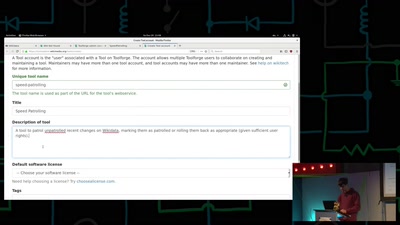
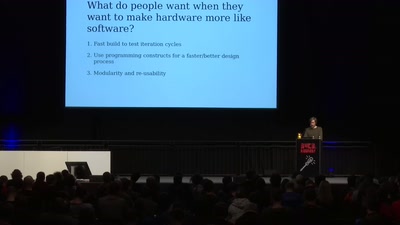
Designing PCBs with code
Is designing circuits with code instead of CAD the future…

61 min
Nintendo Hacking 2016
Game Over
59 min
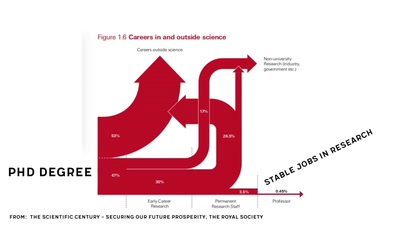
Scientific Literacy 101
Let's understand how the scientific system works
38 min
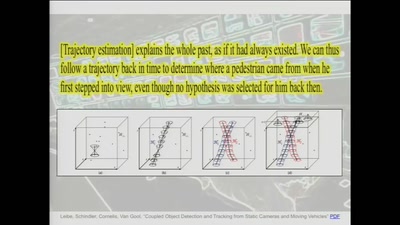
Policing the Romantic Crowd
Velocipedes and Face Recognition

63 min
Building Custom Pinball Machines
What you need and how it works. An experiences report

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

61 min
How Many Planets in Our Solar System? Glad You Asked!
How Astronomy Knew 6 Planets, Then Found 20 More, Then Went…

58 min
Baseband Exploitation in 2013
Hexagon challenges

60 min