Search for "luky" returned 254 results
61 min
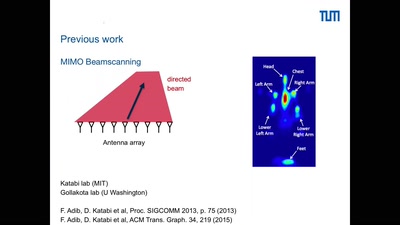
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…
62 min
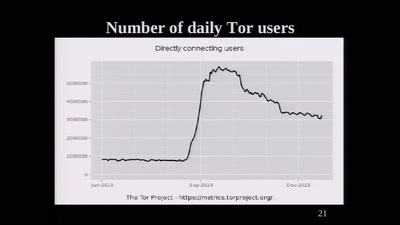
The Tor Network
We're living in interesting times

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

61 min
CAESAR and NORX
Developing the Future of Authenticated Encryption

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

46 min
CounterStrike
Lawful Interception

58 min
Open Source Estrogen
From molecular colonization to molecular collaboration

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

54 min
World War II Hackers
Stalin's best men, armed with paper and pen

55 min