Search for "sECuRE" returned 791 results
39 min
Decentralized energy production: green future or cybersecurity nightmare?
The cybersecurity dark side of solar energy when clouds are…
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

63 min
goto fail;
exploring two decades of transport layer insecurity

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
65 min
Overtaking Proprietary Software Without Writing Code
"a few rough insights on sharpening free software"
45 min
Two decades later - Keysigning in the 2000s
Micro keysigning parties for the masses

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study
24 min
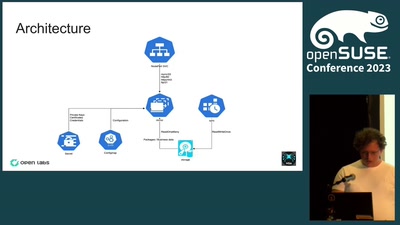
From Physical to Cloud to Container
One system to deploy and manage them all
31 min
Mirror, mirror in the OL
Mirroring in Open Labs Hackerspace

55 min