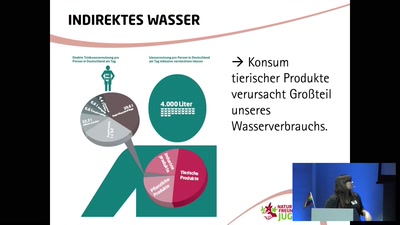
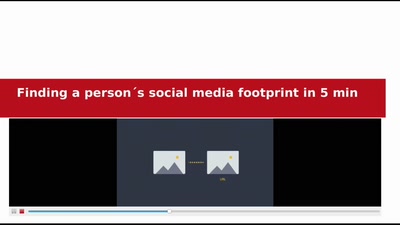
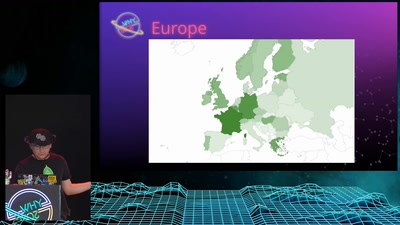
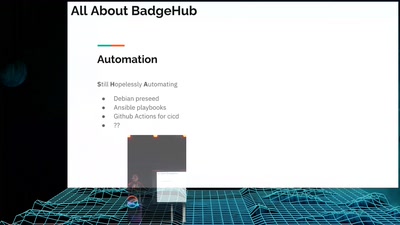
Search for "JO" returned 10053 results

66 min
The Snowden Refugees under Surveillance in Hong Kong
A Rapidly Emerging Police State and Imminent Deportation to…

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

40 min
Psychedelic Medicine - Hacking Psychiatry?!
Psychedelic Therapy as a fundamentally new approach to…
40 min
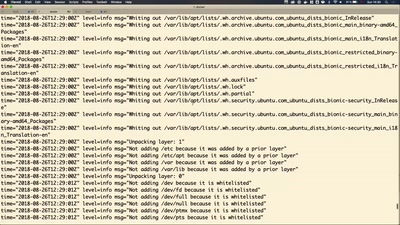
Unboxing and building container images
What is an image technically and how to assemble them…
59 min
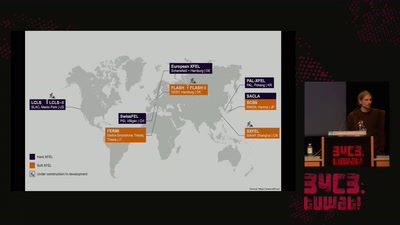
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

43 min
How we changed openSUSE developement
Going from generic distro to stable rolling and feature…
77 min
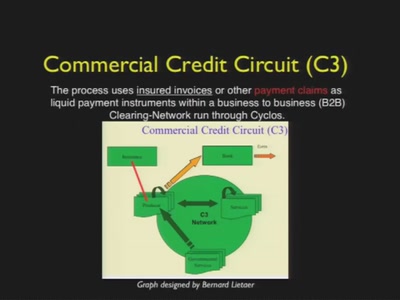
Imagine the Future of Money
Economic transformations, hacker culture and why we should…

60 min
Stromtankstellen – eine neue öffentliche Infrastruktur
Was kann das? Wie kann ich das nutzen? Wo besteht…

60 min
Low Cost High Speed Photography
Using microcontrollers to capture the blink of an eye for…

50 min
Art Tech Activism Privacy and Cool Robots
Not only hackers do Security, Privacy and Hacking. Want to…

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…
59 min
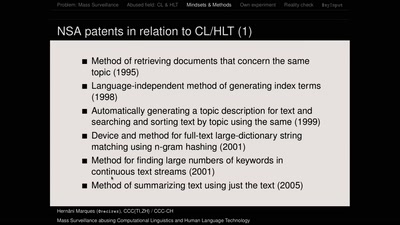
Mass Surveillance abusing Computational Linguistics and Human Language Technology
Mind-sets, state-of-the-art methods and practices according…

33 min
Creating an openSUSE Powered Robot
The joys of open source (taking other peoples work to make…
52 min
Turris: secure open source router
Who is the root on your router?

26 min