Search for "Ike" returned 2797 results

60 min
The Critical Making Movement
How using critical thinking in technological practice can…

32 min
The Case for Scale in Cyber Security
Security Track Keynote

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
31 min
The Economic Consequences of Internet Censorship
Why Censorship is a Bad Idea for Everyone
30 min
Automatically Subtitling the C3
How speech processing helps the CCC subtitle project, and…
62 min
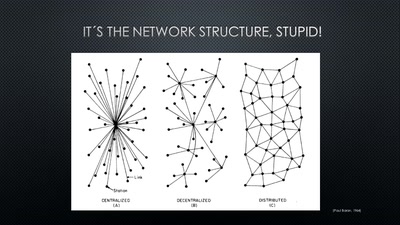
A New Kid on the Block
Conditions for a Successful Market Entry of Decentralized…

60 min
Dieselgate – A year later
env stinks || exit

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis
31 min
Trackography
You never read alone

51 min