Search for "Mo" returned 9987 results
56 min
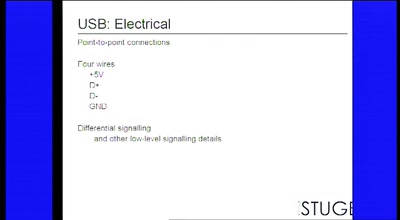
USB and libusb
So much more than a serial port with power

25 min
openSUSE Elections — How are they organised?
Election rules & the election platform
59 min
Ich werde jetzt Embedded-Linux-Entwickler!
“Das kann doch nicht so schwer sein - ist doch auch nur…

61 min
Reducing Carbon in the Digital Realm
How to understand the environmental impact of the digital…
57 min
SageMath Examples from the CrypTool Book
50% Talk 50% Live-Session to try out some code yourself
55 min
Cat & Mouse: Evading the Censors in 2018
Preserving access to the open Internet with circumvention…
32 min
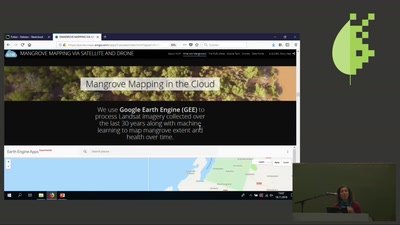
Mangrove Conservation via Satellite
using the latest technology to map and monitor mangroves

27 min
Heroes, not Superheroes
What the Heroes would prefer not to tell you ;-)

57 min
Cybercrime Convention
Hacking on its way to become a criminal act?
45 min
USB-Stick zähmen leicht gemacht
Verteidigung gegen BadUSB & Co. für 30 Euro oder weniger
57 min
Python für das Internet der Dinge
Einführung in MicroPython für ESP8266 und Cortex-M4…

30 min
libusb: Maintainer fail
How I failed to run an open source project

26 min
MariaDB and MySQL — what statistics optimizer needs
or when and how not to use indexes
45 min
Open Source Firmware
... and I finally had my personal bootsplash screen :)

52 min
WASM in the wild
hot-upgradable runtime in substrate thanks to Rust
52 min
Appearance matters!
Use lights to make your shows look better

59 min
System-Level Transactions with picotm
The Days of Plenty Are Yet to Come

26 min






