Search for "Kylli Ek" returned 31 results

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

62 min
Kyber and Post-Quantum Crypto
How does it work?

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

32 min
The Case for Scale in Cyber Security
Security Track Keynote

53 min
Cryptography demystified
An introduction without maths

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks
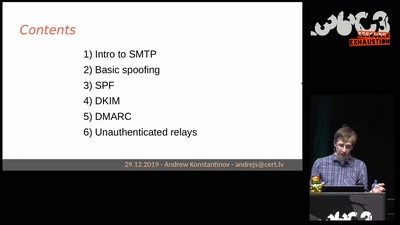
61 min
Email authentication for penetration testers
When SPF is not enough

58 min