Search for "Mirar" returned 40 results

43 min
From Mirai to Apple
How IoT devices bypass Routers

46 min
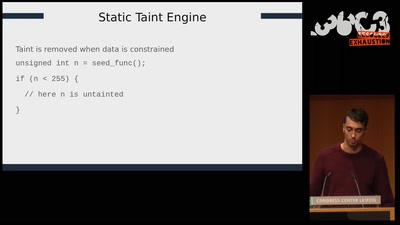
Automated Exploit Detection in Binaries
Finding exploitable vulnerabilities in binaries

119 min
CR236: Intrusion Detection und Incident Response
Who ya gonna call?

119 min
CR242: Einmal einschmelzen bitte
Warum modernes CPU-Design uns jetzt in Teufels Küche bringt

119 min
CR235: I #WannaCry
Der Angriff der Cryptotrojaner

89 min
Usable Privacy and Security
Gebrauchstaugliche sichere Software

42 min
All Creatures Welcome
a utopian documentary about the digital age

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…
59 min
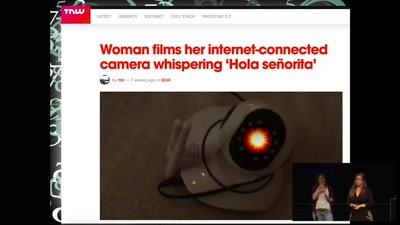
Internet of Fails
Where IoT has gone wrong

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

66 min
The Snowden Refugees under Surveillance in Hong Kong
A Rapidly Emerging Police State and Imminent Deportation to…
42 min