Search for "Naman Jain" returned 117 results

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

53 min
Cryptography demystified
An introduction without maths
58 min
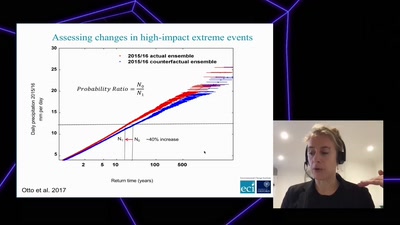
Angry weather ?
How human-induced climate change affects weather (& how we…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

62 min
Kyber and Post-Quantum Crypto
How does it work?

32 min
The Case for Scale in Cyber Security
Security Track Keynote

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

60 min