Search for "Paul Wouters"

69 min
Encrypting (GSM) mobile phone calls over VPN with an…

31 min
Things you always wanted to know about NIC drivers
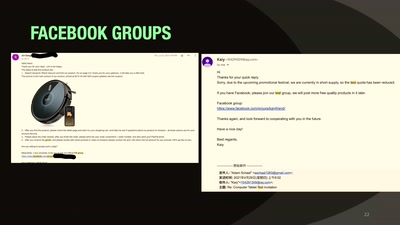
41 min
And the malware and backdoors that came with it.
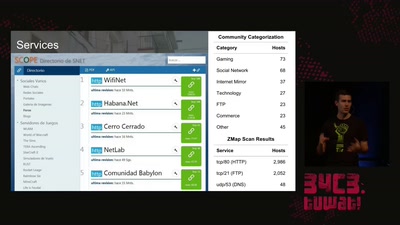
58 min
Get a unique tour of some of the world’s most unusual…

30 min
Visualizing WLAN Channel Usage on OpenWRT
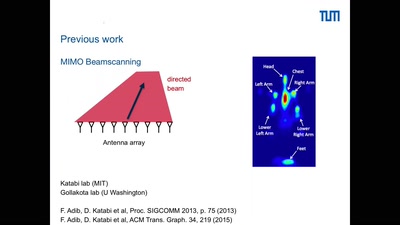
61 min
Can we see the stray radiation of wireless devices? And…

63 min
transparency in the service of justice

60 min
How to drop more of your privileges to reduce attack…

41 min
Side-Channel (and other) Attacks in Practice






