Search for "Victor Toso" returned 170 results

49 min
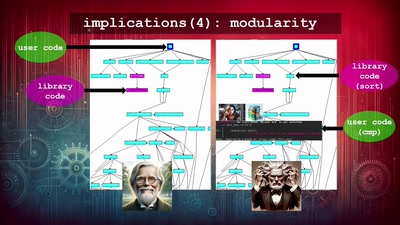
BREACH in Agda
Security notions, proofs and attacks using dependently…
22 min
OpenMapTiles
Revolution in selbstgehosteten Karten

60 min
A Story of Discrimination and Unfairness
Prejudice in Word Embeddings
65 min
LatticeHacks
Fun with lattices in cryptography and cryptanalysis

34 min
Ling - High level system programming
modular and precise resource management

41 min
Why Railway Is Safe But Not Secure
Security Of Railway Communication Protocols

62 min
Kyber and Post-Quantum Crypto
How does it work?

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine

54 min
What Price the Upload Filter?
The history and costs of government exceptional access
56 min