Events for tag "Security & Hacking"

30 min
Privacy Badger
Stop being tracked online
55 min
Cyber Necromancy
Reverse Engineering Dead Protocols
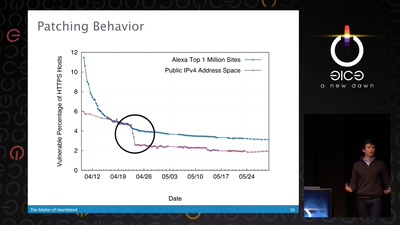
50 min
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

60 min
SS7: Locate. Track. Manipulate.
You have a tracking device in your pocket

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits

31 min
Update: Vor Windows10 Update Warnung
Update (Patch) Debakel

54 min
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks

51 min
Funky File Formats
Advanced binary tricks
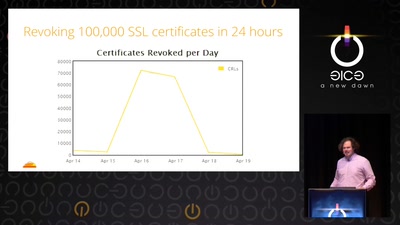
29 min
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

60 min
Vor Windows 8 wird gewarnt
Und nichts (Secure) Bootet mehr?
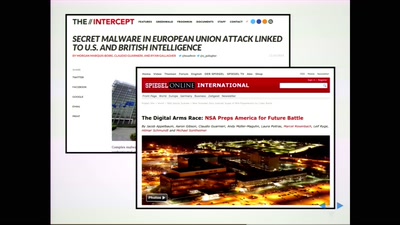
56 min
Helping the Helpless
Targeted threats to civil society
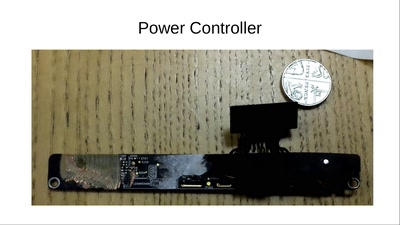
58 min
How to Destroy a Laptop with Top Secrets
How did GCHQ do it to the Guardian's copy of Snowden's…

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

29 min
Jumping the Paywall
How to freely share research without being arrested

58 min
Virtual Machine Introspection
From the Outside Looking In

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety
48 min
Advanced interconnect attacks
Chasing GRX and SS7 vulns

60 min
Ich sehe, also bin ich ... Du
Gefahren von Kameras für (biometrische)…
42 min
Let's Encrypt
A Certificate Authority To Encrypt the Entire Web

58 min
Switches Get Stitches
Industrial System Ownership
46 min
Bugged Files
Is Your Document Telling on You?
28 min
Hardware attacks: hacking chips on the (very) cheap
How to retrieve secret keys without going bankrupt
55 min
How to make your software build reproducibly
Get a verifiable path from source to binary

61 min
Uncaging Microchips
Techniques for Chip Preparation

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets
52 min
TLS interception considered harmful
How Man-in-the-Middle filtering solutions harm the security…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…
61 min