Search for person "David Kim" returned 151 results
23 min
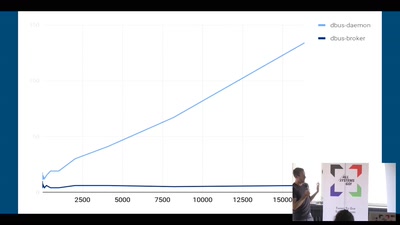
dbus-broker
Status update
61 min
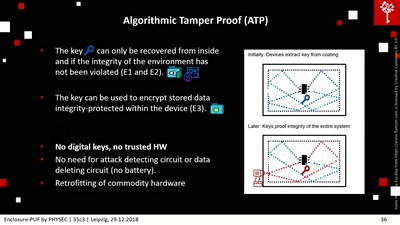
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging
44 min
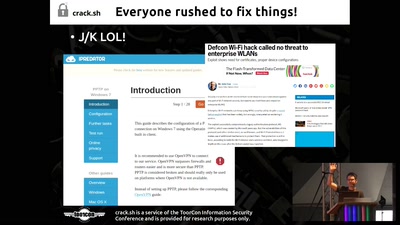
Legacy Crypto Never Dies
Cracking DES nearly 20 years after the EFF DES Cracker

14 min
Open Build Service - Development Roadmap
Past, Present & Future

58 min