Search for person "David Kirschenheuter" returned 128 results

47 min
Peer-to-peer under the hood
An in-depth look at p2p algorithmics

60 min
Faster PwninG Assured
Hardware Hacks and Cracks with FPGAs

61 min
The A5 Cracking Project
Practical attacks on GSM using GNU Radio and FPGAs
98 min
Hardware Hacking for Software Geeks
Essential Tips and Tricks

61 min
MD5 considered harmful today
Creating a rogue CA Certificate
66 min
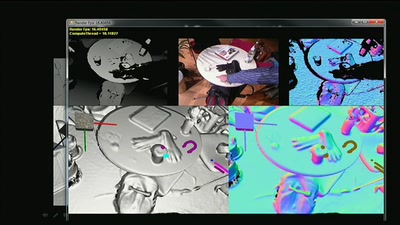
KinectFusion
Real-time 3D Reconstruction and Interaction Using a Moving…

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

49 min
In Love with Ruby
Warum es sich immer noch lohnt, Ruby zu lernen

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…
65 min
Rocket science – how hard can it be?
First steps into space with sounding rockets

63 min
Traue keinem Scan, den du nicht selbst gefälscht hast
"Bei Kopierern kommt das raus, was man reinsteckt." – Wer…
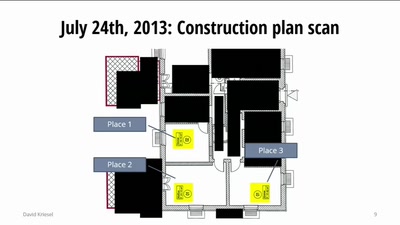
52 min
Lies, damned lies and scans
"A copier's output equals its input." You think that's…

27 min
Social Engineering und Industriespionage
Die unterschätzte Gefahr

38 min
On Computable Numbers with an Application to the Modelleisenbahn
Turing Train Terminal

58 min