Search for person "Dr. Roland van Rijswijk-Deij" returned 298 results

63 min
Biometrics in Science Fiction
2nd Iteration
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007

42 min
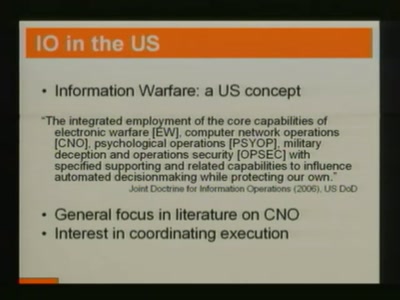
Just in Time compilers - breaking a VM
Practical VM exploiting based on CACAO

44 min
Why technology sucks
If technology is the solution, politicians are the problem
73 min
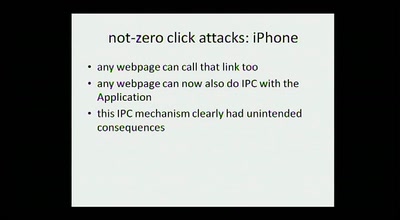
hacking smart phones
expanding the attack surface and then some
51 min
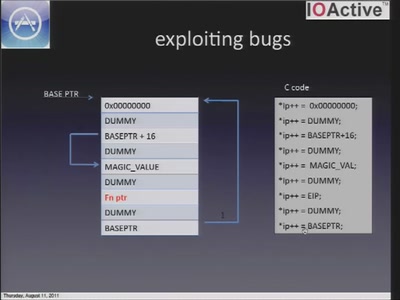
iOS application security
A look at the security of 3rd party iOS applications

56 min
Openmoko: 5 years after – What's left behind.
Free software and hardware projects for mobile communication

38 min
Der Inhalt dieses Vortrags ist in deinem Land leider nicht verfügbar.
oder wie man in einen Walfisch klettert, ohne ihn dabei zu…

56 min
eAnalytics
Integrierte Open Source Webanalyse

58 min
Setting mobile phones free
An overview of a mobile telephony market and how a…

55 min
Our daily job: hacking the law
The key elements of policy hacking

59 min
Security Evaluation of Russian GOST Cipher
Survey of All Known Attacks on Russian Government…

31 min
C.R.O.P. – Combined Regenerative Organic-food Production
C.R.O.P., ein Forschungsprojekt des Deutschen Zentrums für…
61 min
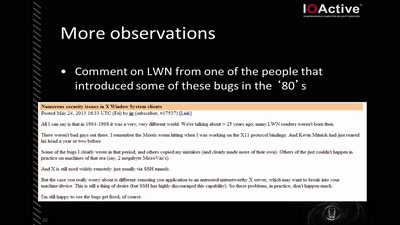
X Security
It's worse than it looks
67 min