Search for person "Roland van Rijswijk-Deij" returned 138 results

63 min
Biometrics in Science Fiction
2nd Iteration
53 min
Crouching Powerpoint, Hidden Trojan
An analysis of targeted attacks from 2005 to 2007

42 min
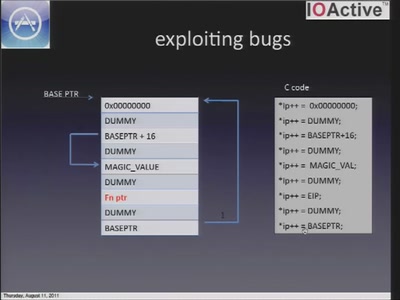
Just in Time compilers - breaking a VM
Practical VM exploiting based on CACAO

44 min
Why technology sucks
If technology is the solution, politicians are the problem
73 min
hacking smart phones
expanding the attack surface and then some
51 min
iOS application security
A look at the security of 3rd party iOS applications

38 min
Der Inhalt dieses Vortrags ist in deinem Land leider nicht verfügbar.
oder wie man in einen Walfisch klettert, ohne ihn dabei zu…

58 min
Setting mobile phones free
An overview of a mobile telephony market and how a…

55 min
Our daily job: hacking the law
The key elements of policy hacking
61 min
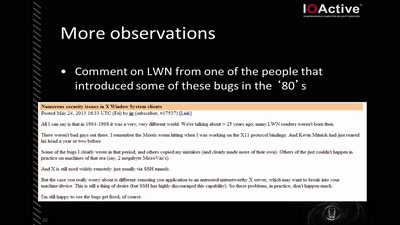
X Security
It's worse than it looks

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

45 min
Time affects
Human-computer-synchronizations
61 min
Avoiding kernel panic: Europe’s biggest fails in digital policy-making
How the institutions fuck up, and how we fuck it up as well

60 min
Windows drivers attack surface
some 'new' insights

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

63 min