Search for person "Steven Ottens" returned 13 results
57 min
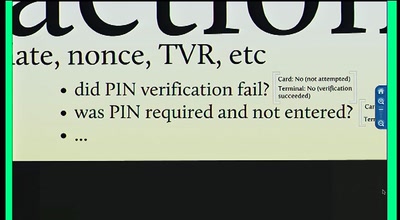
Chip and PIN is Broken
Vulnerabilities in the EMV Protocol

58 min
Security Failures in Smart Card Payment Systems
Tampering the Tamper-Proof
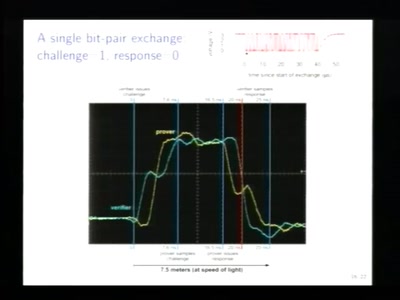
62 min
Relay attacks on card payment: vulnerabilities and defences
Keeping your enemies close

62 min
Detecting temperature through clock skew
Hot or Not: Defeating anonymity by monitoring clock skew to…

42 min
Covert channels in TCP/IP: attack and defence
Creation and detection of IP steganography for covert…

45 min