Search for "Ike" returned 2797 results

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
60 min
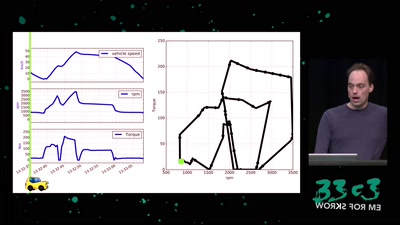
Software Defined Emissions
A hacker’s review of Dieselgate

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…

45 min
To Protect And Infect
The militarization of the Internet
59 min
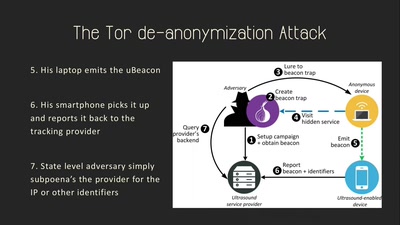
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish
61 min
X Security
It's worse than it looks

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice
63 min
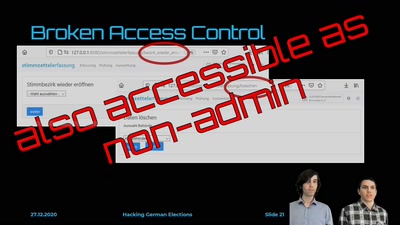
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…
25 min