Search for "kay" returned 3829 results

64 min
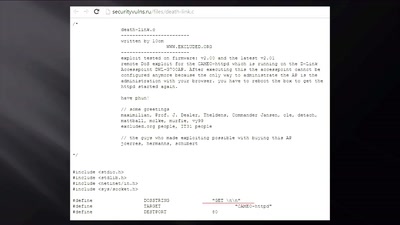
"Exploit" in theater
post-existentialism is the question, not post-privacy

53 min
Cryptography demystified
An introduction without maths

54 min
What Price the Upload Filter?
The history and costs of government exceptional access

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers
61 min
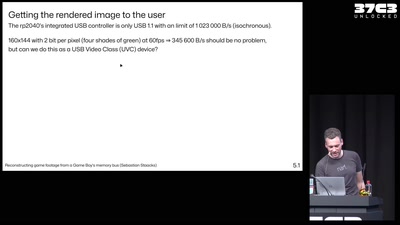
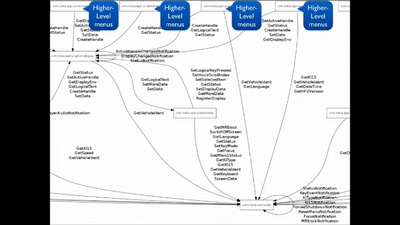
Reconstructing game footage from a Game Boy's memory bus
The GB Interceptor
58 min
Script Your Car!
Using existing hardware platforms to integrate python into…

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

54 min
A la recherche de l'information perdue
some technofeminist reflections on Wikileaks

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

39 min
Brennende Wälder und Kommentarspalten
Klimaupdate mit dem FragDenStaat Climate Helpdesk
66 min
Hacking Diversity: The Politics of Inclusion in Open Technology Cultures
Christina Dunbar-Hester
64 min
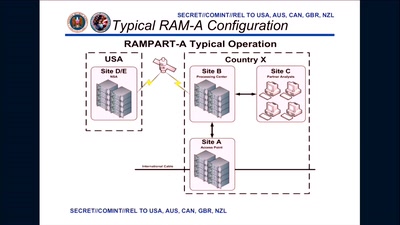
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…

62 min