Search for "@FiLiS" returned 614 results
47 min
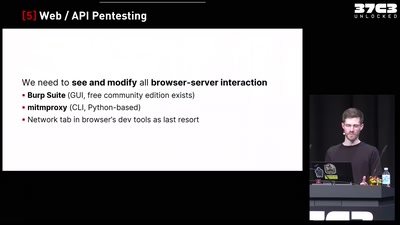
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide
60 min
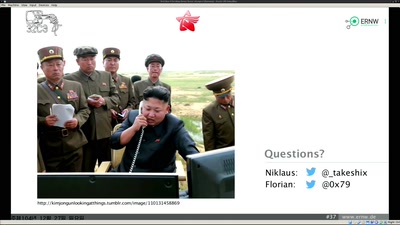
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…

36 min
Modchips of the State
Hardware implants in the supply-chain
33 min
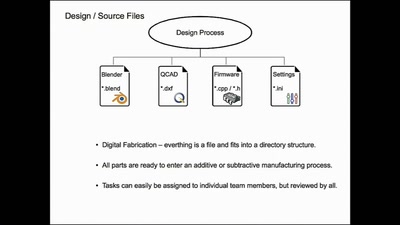
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…

47 min
The KGB Hack: 30 Years Later
Looking back at the perhaps most dramatic instance of…
61 min
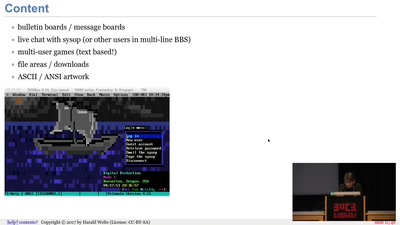
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

33 min
Robot Music
The Robots Play Our Music and What Do We Do?

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

63 min
Reconstructing narratives
transparency in the service of justice

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

62 min