Search for "Luca" returned 355 results

45 min
To Protect And Infect
The militarization of the Internet

61 min
Vacuum robot security and privacy
prevent your robot from sucking your data

72 min
Console Hacking
Breaking the 3DS

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
56 min
The mummy unwrapped
Cultural Commons durch Kunstraub

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…

58 min
Baseband Exploitation in 2013
Hexagon challenges
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology

46 min
Taking a scalpel to QNX
Analyzing & Breaking Exploit Mitigations and Secure Random…
65 min
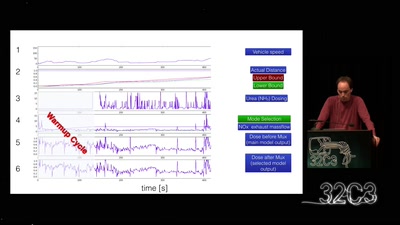
The exhaust emissions scandal („Dieselgate“)
Take a deep breath into pollution trickery
53 min
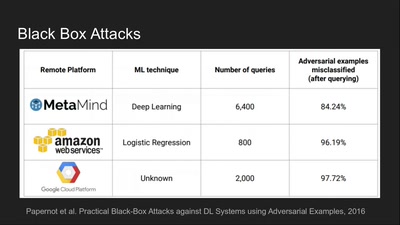
Deep Learning Blindspots
Tools for Fooling the "Black Box"

58 min
Überwachen und Sprache
How to do things with words

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

54 min