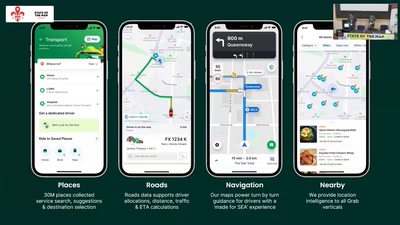
Search for "Kay" returned 3681 results

32 min
Live: Avahi / Zeroconf: Some magic sauce that's about more than files and printers
Hand editing config files for local deployment? Say hi to…

37 min
Self-documenting computation
What is the best way to present programs to non-programmers?
31 min
Growing Up Software Development
From Hacker Culture to the Software of the Future
![NSFW: Di[CENSORED]s for privacy](https://static.media.ccc.de/media/events/SHA2017/49-hd.jpg)
28 min
NSFW: Di[CENSORED]s for privacy
Why not give hackers and agencies something to look at . .

58 min
Cray-1, Ikone des Supercomputing
Wie die Maschine zur Welt kam, und was danach passierte

59 min
Vulnerability markets
What is the economic value of a zero-day exploit?

61 min
Human body as an electric IO system
Hacking your brain, and other body parts. Debunking myths…
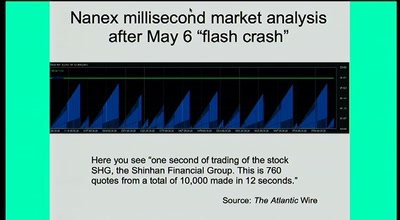
60 min
Three jobs that journalists will do in 2050
Why future media may be more powerful (and more subversive)…

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

31 min
The DRM Of Pacman
Copy protection schemes of way back then and how they…
29 min