Search for "mel" returned 2534 results
36 min
Wheel of Fortune
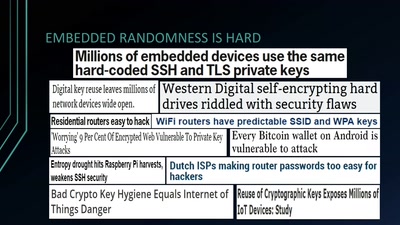
Analyzing Embedded OS Random Number Generators

33 min
Retail Surveillance / Retail Countersurveillance
50 most unwanted retail surveillance technologies / 50 most…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

65 min
The Untold Story of Edward Snowden’s Escape from Hong Kong
and How You Can Help the Refugees Who Saved His Life

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

40 min
Intercoms Hacking
Call the frontdoor to install your backdoors
62 min
Machine Dreams
Dreaming Machines

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

58 min
SpiegelMining – Reverse Engineering von Spiegel-Online
Wer denkt, Vorratsdatenspeicherungen und „Big Data“ sind…
86 min
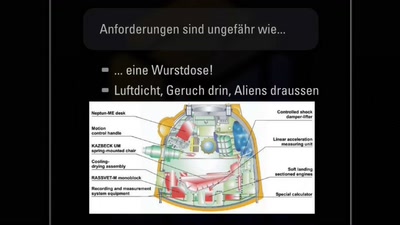
Wie baut man eigentlich Raumschiffe
Teil 1: Die Hülle

49 min
Barrierefreiheit bei OpenTalk
Lessons Learned

38 min
Die wunderliche Welt der Netzteilhieroglyphen
Was die ganzen Labels, Logos und Emojis auf einem Gerät…

119 min