Search for "Mark" returned 1127 results

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity

51 min
Smart Home - Smart Hack
Wie der Weg ins digitale Zuhause zum Spaziergang wird
30 min
“Nabovarme” opensource heating infrastructure in Christiania
Freetown Christiania´s digitally controlled/surveyed…
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now

38 min
Gerechtigkeit 4.0
Makroökonomische Auswirkungen der Digitalisierung auf den…

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

61 min
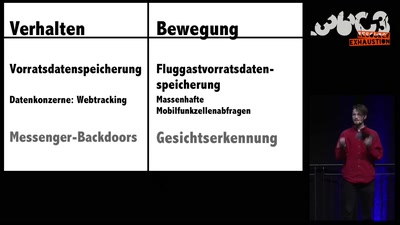
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…
113 min
Das Bits&Bäume-Sporangium
8 Mikrokosmen, 8 Expert*innen, je 8 Minuten zu…
42 min
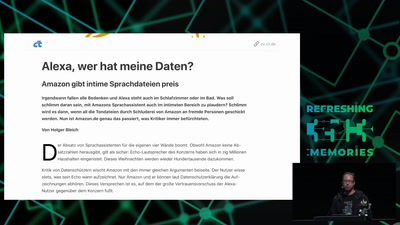
Netzpolitischer Wetterbericht 2018
Die Höhen und Tiefen der deutschen und europäischen…

26 min
Humans as software extensions
Will You Be My Plugin?
25 min
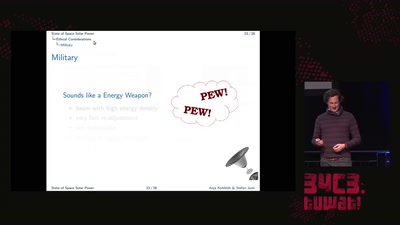
Saving the World with Space Solar Power
or is it just PEWPEW?!
61 min
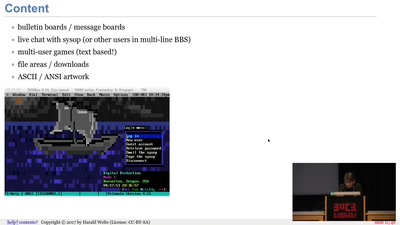
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

62 min
Superheroes Still Need Phoneboxes
The art of making a free phonebox and the culture of…
61 min
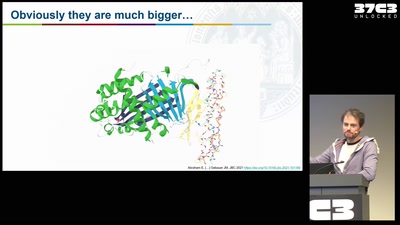
AlphaFold – how machine learning changed structural biology forever (or not?)
Getting first-hand insights into the impact of machine…
48 min
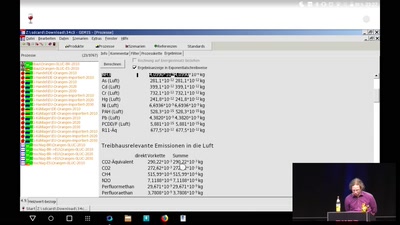
Treibhausgasemissionen einschätzen
Wieviel CO2 macht <...>? Ungefähr?

54 min