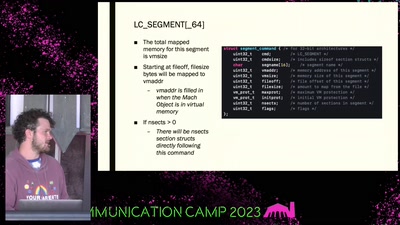
Search for "Hugo" returned 771 results
59 min
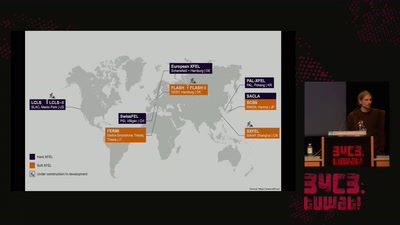
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

30 min
Syrian Archive
Preserving documentation of human rights violations

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

63 min
Don't stop 'til you feel it
Artistic interventions in climate change

59 min
Provable Security
How I learned to stop worrying and love the backdoor

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge
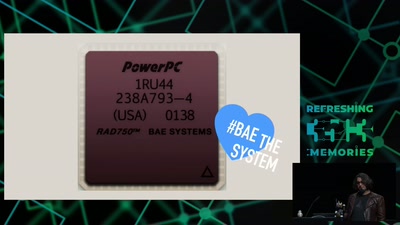
43 min
The Mars Rover On-board Computer
How Curiosity's Onboard Computer works, and what you can…

30 min
Privacy and Consumer Markets
Reversing the Surveillance Business Model
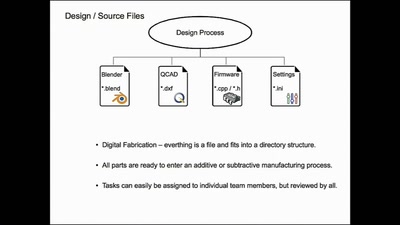
33 min
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…
45 min