Search for "Math" returned 1306 results

101 min
Chaos Communication Slam
Technische Liebesgedichte & Horrorgeschichten im…

60 min
HAL - The Open-Source Hardware Analyzer
A dive into the foundations of hardware reverse engineering…

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…

52 min
The Internet of rubbish things and bodies
A review of the best art & tech projects from 2019. With a…

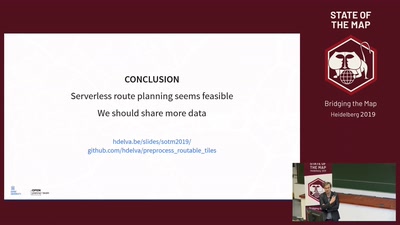
59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it

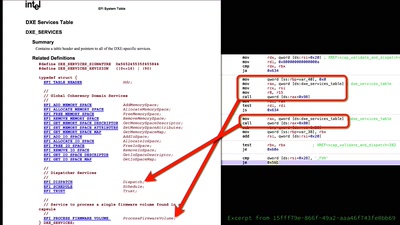
46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
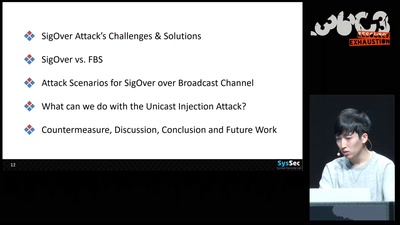
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications
46 min