Search for "Udo Vetter" returned 1175 results

60 min
Buffering sucks!
An attempt of calculating the economic cost of buffering.

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…
61 min
Numerical Air Quality Modeling Systems
a journey from emissions to exposure

56 min
Household, Totalitarianism and Cyberspace
Philosophical Perspectives on Privacy Drawing on the…

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science
61 min
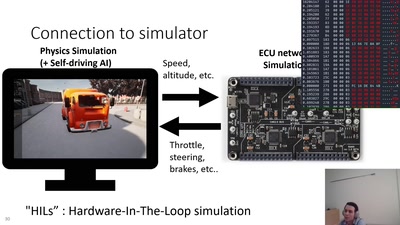
RAMN: Resistant Automotive Miniature Network
A safe platform to study and research automotive systems
42 min
Domain Name System
Hierarchical decentralized naming system used since 30 years

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices
61 min
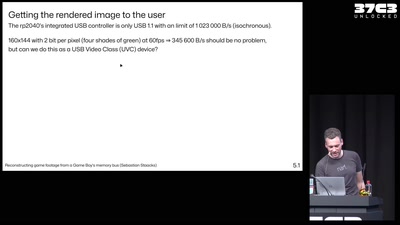
Reconstructing game footage from a Game Boy's memory bus
The GB Interceptor

33 min
institutions for Resolution Disputes
Rosa Menkman investigates video compression, feedback, and…
47 min