Search for "Jim" returned 4890 results

103 min
Comparison of WAN IGP protocols
RSTP+flooding/learning for Ethernet, OSPFv2 for IPv4, and…

55 min
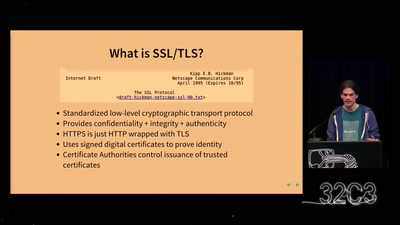
The DROWN Attack
Breaking TLS using SSLv2

61 min
Programming FPGAs with PSHDL
Let's create the Arduino for FPGAs

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

38 min
Afroroutes: Africa Elsewhere
VR experience "Beyond Slavery"

26 min
Data Mining for Good
Using random sampling, entity resolution, communications…
60 min
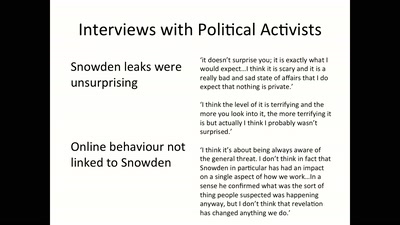
Media Coverage and the Public in the Surveillance Society
Findings from a Research Project on Digital Surveillance…

31 min
Mr Beam goes Kickstarter
Lessons learned from crowdfunding a hardware project

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…

36 min
A Blockchain Picture Book
Blockchain origins and related buzzwords, described in…
35 min
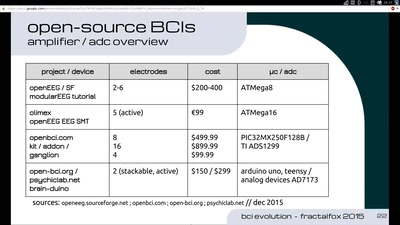
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…
60 min
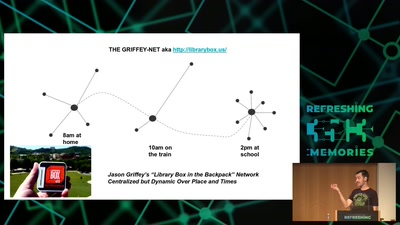
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min