Search for "wsa" returned 5281 results
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

115 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 34C3
35 min
Ethics in the data society
Power and politics in the development of the driverless car
36 min
Long Distance Quantum Communication
Concepts and components for intercontinal communication…

31 min
TrustZone is not enough
Hijacking debug components for embedded security

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

33 min
Beyond Virtual and Augmented Reality
From Superhuman Sports to Amplifying Human Senses
41 min
SCADA StrangeLove 2
We already know

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
31 min
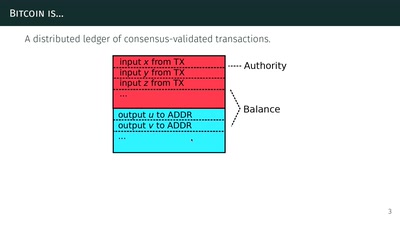
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…
35 min
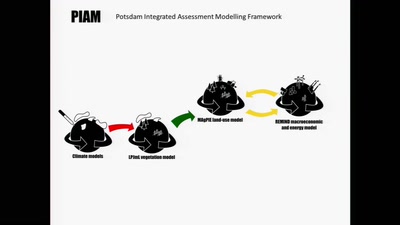
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

44 min
ASLR on the line
Practical cache attacks on the MMU
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis

60 min
Shopshifting
The potential for payment system abuse

44 min