Search for "Adam Wight" returned 120 results

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild

32 min
Visceral Systems
Approaches to working with sound and network data…

60 min
Lets break modern binary code obfuscation
A semantics based approach
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways

46 min
Climate Modelling
The Science Behind Climate Reports
52 min
Leaving legacy behind
Reducing carbon footprint of network services with MirageOS…

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…
61 min
Reconstructing game footage from a Game Boy's memory bus
The GB Interceptor
59 min
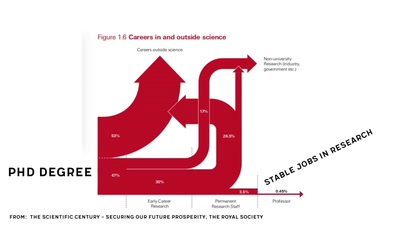
Scientific Literacy 101
Let's understand how the scientific system works

63 min
Reconstructing narratives
transparency in the service of justice

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

29 min
What de.fac2?
Attacking an opensource U2F device in 30 minutes or less
38 min
ARMore: Pushing Love Back Into Binaries
Aarch64 binary rewriting adventures but mostly pains
41 min
Infrastructure of a migratory bird
Technology and autonomy in more-than-human networks
38 min