Search for "Lia Strenge" returned 227 results

54 min
How hackers grind an MMORPG: by taking it apart!
An introduction to reverse engineering network protocols
56 min
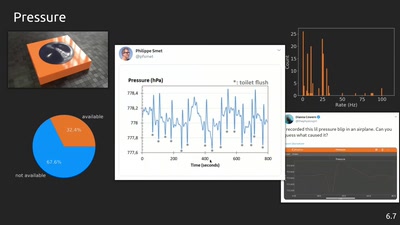
phyphox: Using smartphone sensors for physics experiments
An open source project for education, research and tinkering

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.
61 min
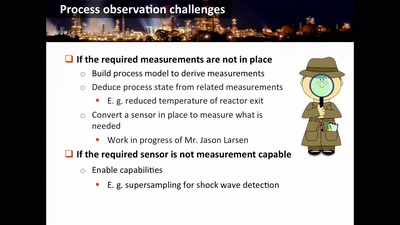
Damn Vulnerable Chemical Process
Exploitation in a new media

55 min
The DROWN Attack
Breaking TLS using SSLv2
41 min
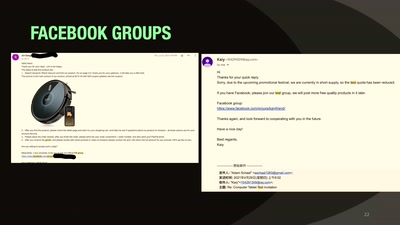
Our Time in a Product Review Cabal
And the malware and backdoors that came with it.

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…
66 min
31C3 Keynote
A New Dawn

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

30 min
libusb: Maintainer fail
How I failed to run an open source project

63 min
Analyze the Facebook algorithm and reclaim data sovereignty
Algorithms define your priorities. Who else besides you can…

59 min
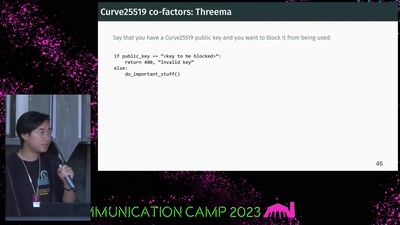
Provable Security
How I learned to stop worrying and love the backdoor
43 min
If It Ain't Broken, Do Fix It
Building Modern Cryptography
58 min
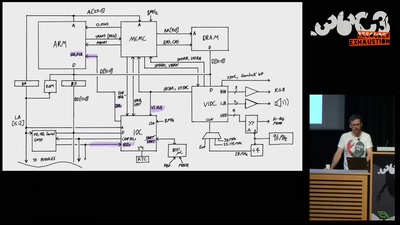
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…
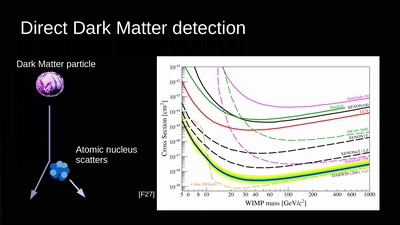
60 min
Let's reverse engineer the Universe
exploring the dark
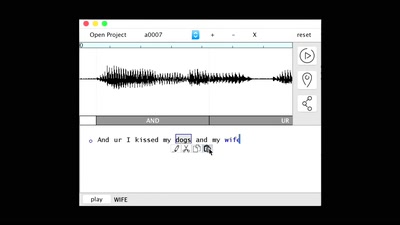
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

32 min
Visceral Systems
Approaches to working with sound and network data…
27 min