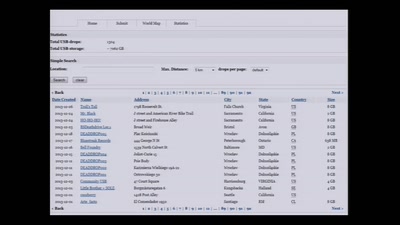
Search for "Phil" returned 55 results

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
57 min
Hello World!
How to make art after Snowden?

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
60 min
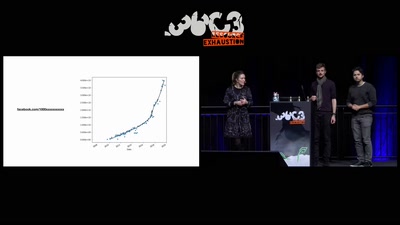
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

46 min
Digital Airwaves
Software Defined Radio Basics and some Modulation Theory
61 min
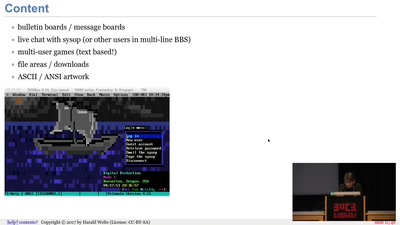
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN
37 min
Schweiz: Netzpolitik zwischen Bodensee und Matterhorn
Massenüberwachung, Netzsperren und andere netzpolitische…

61 min
Vacuum robot security and privacy
prevent your robot from sucking your data
56 min
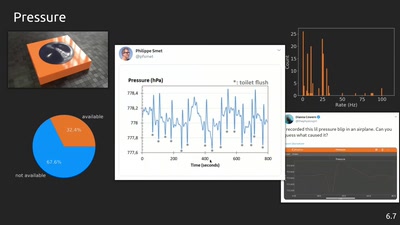
phyphox: Using smartphone sensors for physics experiments
An open source project for education, research and tinkering

54 min