Search for "cy" returned 5992 results

60 min
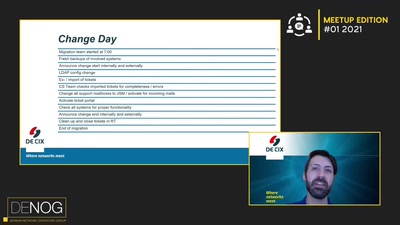
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

55 min
White-Box Cryptography
Survey

58 min
Virtual Machine Introspection
From the Outside Looking In
35 min
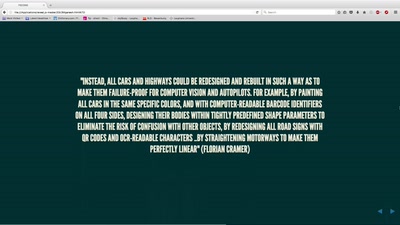
Ethics in the data society
Power and politics in the development of the driverless car

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

35 min
Internet of toilets
Trends in the sanitarian territory
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!

57 min
"Fluxus cannot save the world."
What hacking has to do with avantgarde art of the 1960ies…

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
57 min
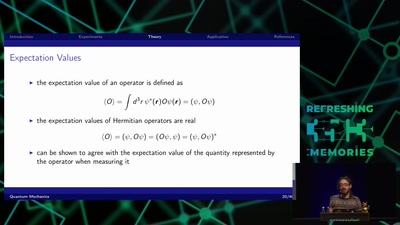
Quantum Mechanics
A Gentle Introduction
41 min
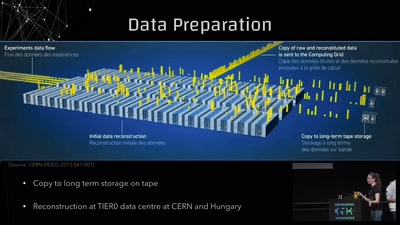
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research
32 min
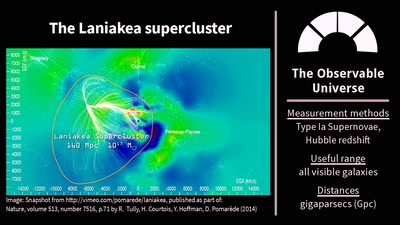
The Universe Is, Like, Seriously Huge
Stuff in Space Is Far Away – but How Do We Know?

59 min
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
29 min