Search for "ALH" returned 5832 results

60 min
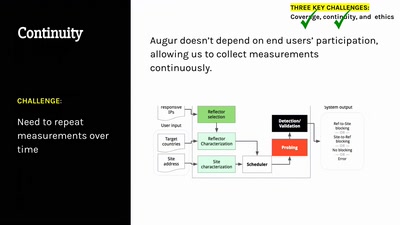
Beyond Anti Evil Maid
Making it easier to avoid low-level compromise, and why…
66 min
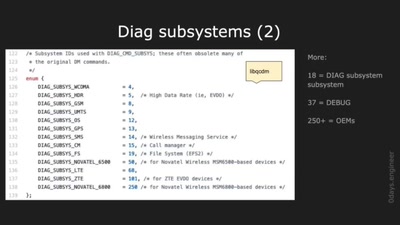
Advanced Hexagon Diag
Harnessing diagnostics for baseband vulnerability research

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

56 min
WarGames in memory
what is the winning move?

60 min