Search for "Andi Rüther" returned 708 results

33 min
UPSat - the first open source satellite
Going to space the libre way
35 min
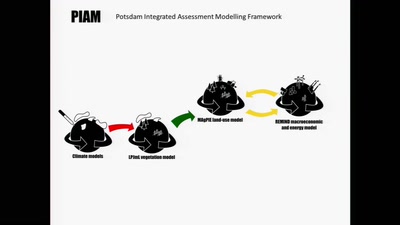
Simulating the future of the global agro-food system
Cybernetic models analyze scenarios of interactions between…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…
62 min
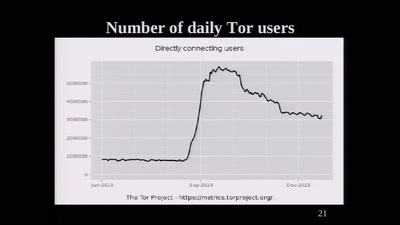
The Tor Network
We're living in interesting times

51 min
The GNU Name System
A Decentralized PKI For Social Movements

55 min
Attribution revolution
Turning copyright upside-down with metadata

54 min
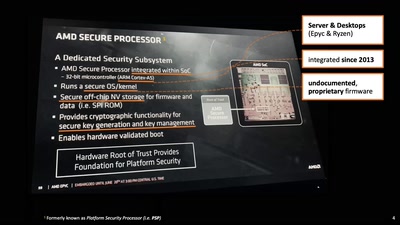
AMD x86 SMU firmware analysis
Do you care about Matroshka processors?
61 min
Rocket Kitten: Advanced Off-the-Shelf Targeted Attacks Against Nation States
A Deep Technical Analysis

33 min
Turing Complete User
What can be done to protect the term, the notion and the…

32 min
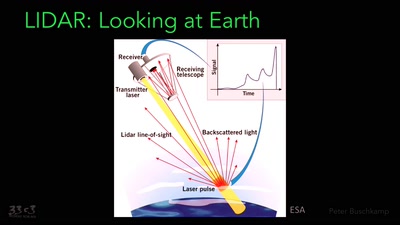
The Moon and European Space Exploration
Refocusing on the moon as a platform for future deep space…
44 min
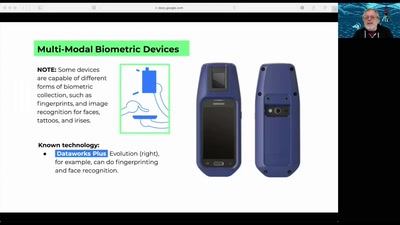
Spot the Surveillance
How to Identify Police Surveillance at Protests and Large…
60 min
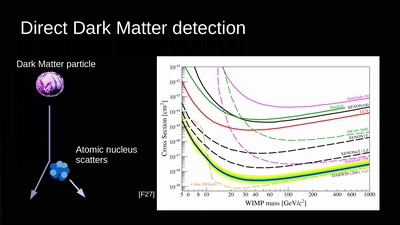
Let's reverse engineer the Universe
exploring the dark
40 min
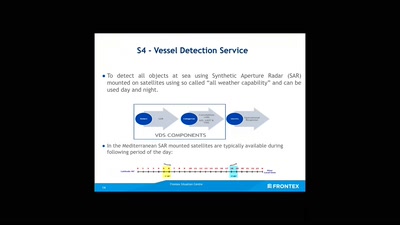
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

33 min