Search for "Kemo" returned 658 results

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

54 min
Tactical Embodiment
Activism and Performance In Hostile Spaces Online

60 min
Österreich: Der Kampf gegen unkontrollierte Massenüberwachung
Geheimdienste kontrolliert man am besten, indem man ihre…
60 min
The Perl Jam 2
The Camel Strikes Back
77 min
Entbehrliches
Unterhaltsames Wissen aus der Wikipedia
66 min
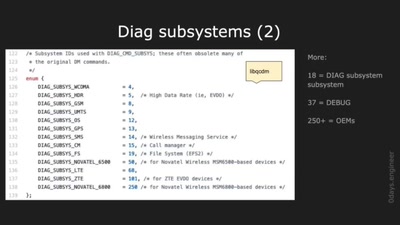
Advanced Hexagon Diag
Harnessing diagnostics for baseband vulnerability research

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP
60 min
Netzpolitik in der Schweiz
NDG, BÜPF und wie wir uns dagegen wehren
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

58 min
Funkzellenabfrage: Die alltägliche Rasterfahndung unserer Handydaten
Wie wir alle regelmäßig den Behörden ins Netz gehen und wie…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…
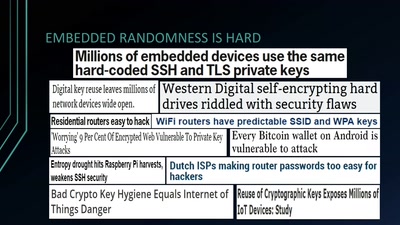
36 min
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

55 min