Search for "Udo Vetter" returned 1176 results

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…
39 min
Gamified Control?
China's Social Credit Systems
56 min
Iridium Update
more than just pagers
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
31 min
Nerds in the news
Spending a year coding in a newsroom
52 min
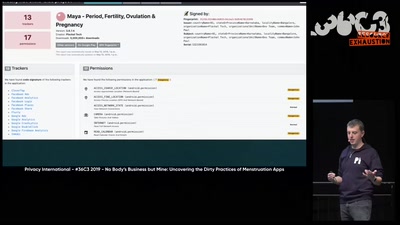
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…

60 min