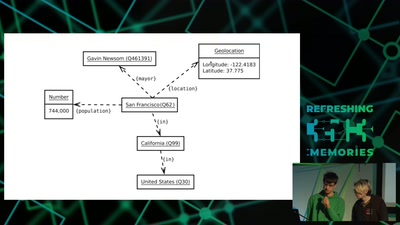
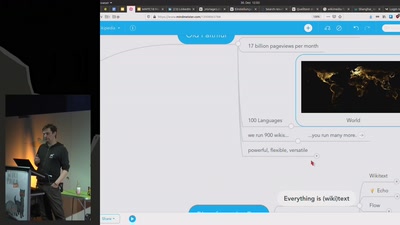
Search for "Hugo" returned 771 results

27 min
Italy's surveillance toolbox
Research on Monitoring Italian Government Surveillance…
31 min
Growing Up Software Development
From Hacker Culture to the Software of the Future
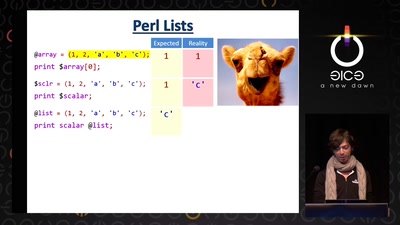
60 min
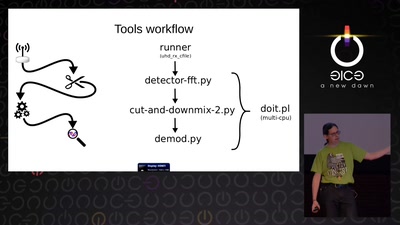
The Perl Jam 2
The Camel Strikes Back

54 min
What Price the Upload Filter?
The history and costs of government exceptional access
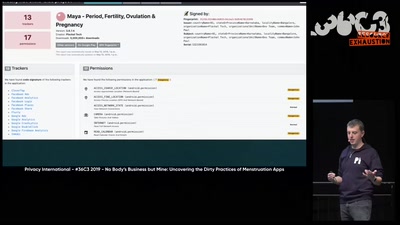
52 min
No Body's Business But Mine, a dive into Menstruation Apps
The Not-So Secret Data Sharing Practices Of Menstruation…
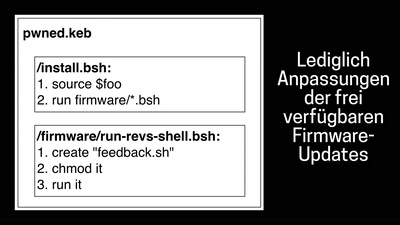
52 min
Ladeinfrastruktur für Elektroautos: Ausbau statt Sicherheit
Warum das Laden eines Elektroautos unsicher ist

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

24 min
The Four Wars
Terror, whistleblowers, drugs, internet

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…
47 min
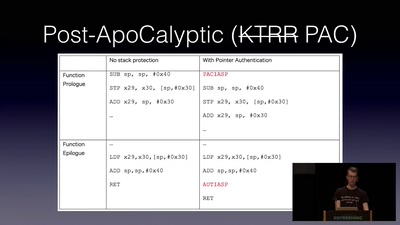
Jailbreaking iOS
From past to present
45 min
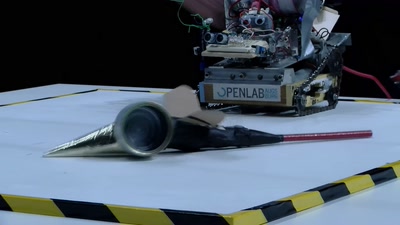
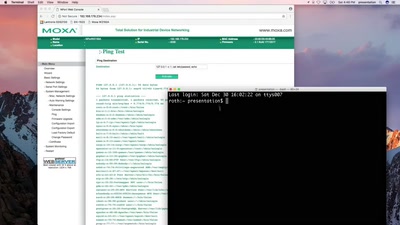
SCADA - Gateway to (s)hell
Hacking industrial control gateways
37 min