Search for "sECuRE" returned 792 results

58 min
Cyber all the Wassenaars
Export controls and exploit regulations: braindead and…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

54 min
What Price the Upload Filter?
The history and costs of government exceptional access
60 min
Lifting the Fog on Red Star OS
A deep dive into the surveillance features of North Korea's…
72 min
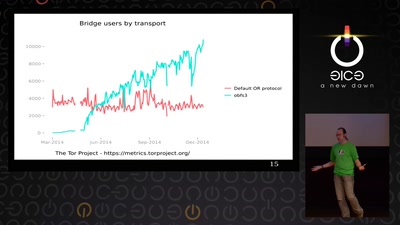
State of the Onion
Neuland

26 min
Hacking the World
The struggle for security for all.
59 min
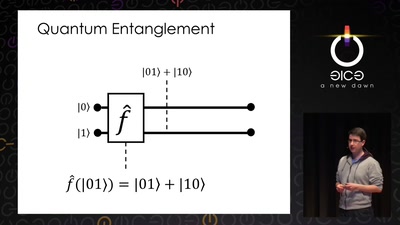
Let's build a quantum computer!
Understanding the architecture of a quantum processor

53 min
Console Hacking 2016
PS4: PC Master Race

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice
35 min
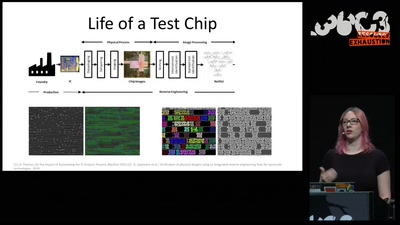
Understanding millions of gates
Introduction to IC reverse engineering for…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…
21 min
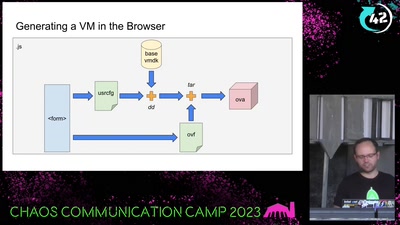
Bootloader Crimes
Building disposable Windows VMs

60 min
Windows drivers attack surface
some 'new' insights
66 min
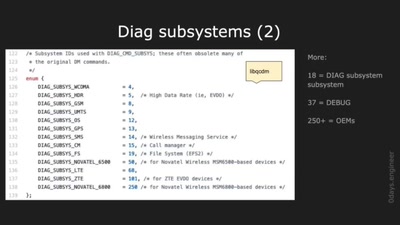
Advanced Hexagon Diag
Harnessing diagnostics for baseband vulnerability research
60 min
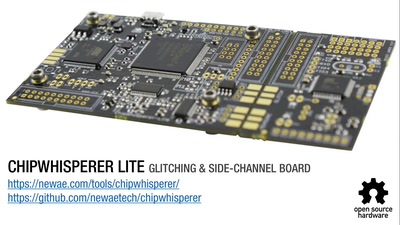
Opening Closed Systems with GlitchKit
'Liberating' Firmware from Closed Devices with Open Source…

50 min
Internet censorship in the Catalan referendum
Overview of how the state censored and how it got…

46 min
CounterStrike
Lawful Interception

49 min