Search for "Andi Rüther" returned 708 results
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century

58 min
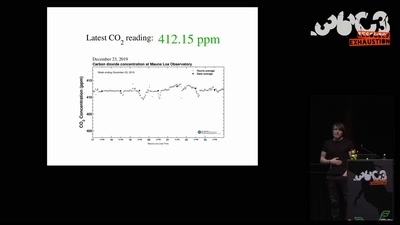
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine

55 min
What is Good Technology?
Answers & practical guidelines for engineers.
56 min
Iridium Update
more than just pagers
29 min
Blinkenrocket!
How to make a community project fly

59 min
Memory Deduplication: The Curse that Keeps on Giving
A tale of 3 different memory deduplication based…
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice
46 min
What The Fax?!
Hacking your network likes it's 1980 again

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

46 min
CounterStrike
Lawful Interception

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

46 min