Search for "Ute Holl" returned 1361 results

62 min
Bionic Ears
Introduction into State-of-the-Art Hearing Aid Technology

62 min
Kyber and Post-Quantum Crypto
How does it work?
61 min
AlphaFold – how machine learning changed structural biology forever (or not?)
Getting first-hand insights into the impact of machine…

60 min
On Digitalisation, Sustainability & Climate Justice
A critical talk about sustainability, technology, society,…

58 min
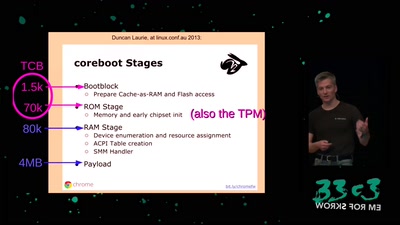
Baseband Exploitation in 2013
Hexagon challenges

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine

31 min
Sysadmins of the world, unite!
a call to resistance

31 min
BGP and the Rule of Custom
How the internet self-governs without international law

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

29 min
Der netzpolitische Wetterbericht
Wird es Regen geben? Ein Ausblick auf die neue…

107 min
Nougatbytes 11₂
Die geekige Wort- & Bilderrätselspielshau ist zuЯück
60 min