Search for "Andi Rüther" returned 708 results

56 min
WarGames in memory
what is the winning move?
62 min
Public Library/Memory of the World
Access to knowledge for every member of society

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative
60 min
So you want to build a satellite?
How hard can it be? An introduction into CubeSat development

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
62 min
Machine Dreams
Dreaming Machines

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

69 min
Telescope Making
How to make your own telescope

61 min
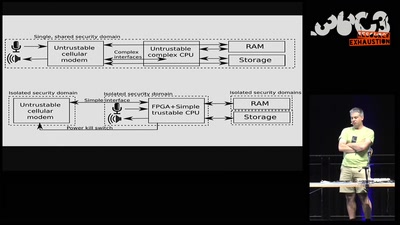
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

60 min
The Critical Making Movement
How using critical thinking in technological practice can…

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…
61 min
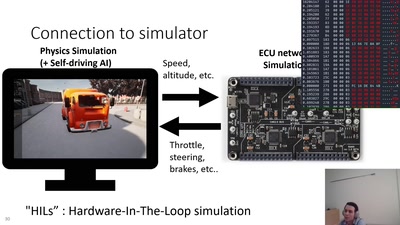
RAMN: Resistant Automotive Miniature Network
A safe platform to study and research automotive systems
49 min
Creating Resilient and Sustainable Mobile Phones
Be prepared for the coming Digital Winter. And play…

60 min
What does Big Brother see, while he is watching?
Uncovering images from the secret Stasi archives.

62 min