Search for "Hugo" returned 771 results
32 min
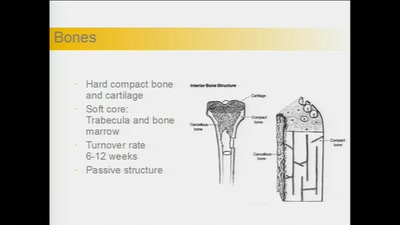
Coding your body
How to decipher the messages of your body

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

49 min
Electromagnetic Threats for Information Security
Ways to Chaos in Digital and Analogue Electronics
31 min
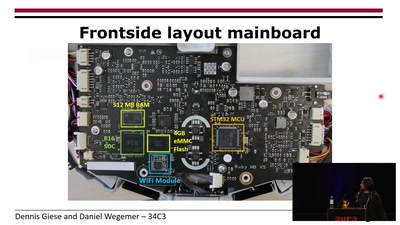
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

33 min
UPSat - the first open source satellite
Going to space the libre way

31 min
The Clash of Digitalizations
The Devolution of Arab Men from Humans to Digital Fodder
35 min
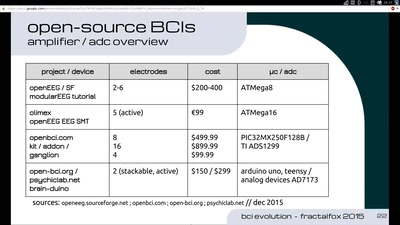
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…
42 min
Union Busting
What is it and why you should care

55 min
Fuzzing the phone in the iPhone
D-d-d-di-di-d-d-di-d-di-d-di-d-dimm!

60 min
Are machines feminine?
exploring the relations between design and perception of…

60 min
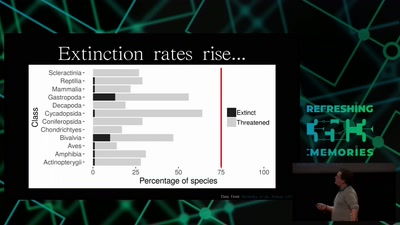
The Critical Making Movement
How using critical thinking in technological practice can…
60 min