Search for "Nico" returned 1170 results
38 min
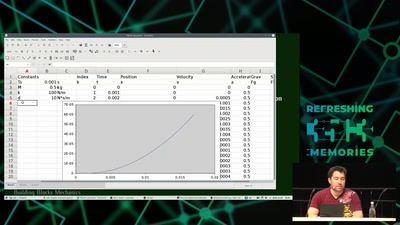
Modeling and Simulation of Physical Systems for Hobbyists
Essential Tools for Developing, Testing and Debugging…
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

32 min
Visceral Systems
Approaches to working with sound and network data…

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

30 min
All Our Shared Spectrum Are Belong to Us
Visualizing WLAN Channel Usage on OpenWRT
58 min
CHINTERNET ART
Creativity, Archives & Digital Media from the Chinese…

42 min
Jugend Hackt
Chaos Family
55 min
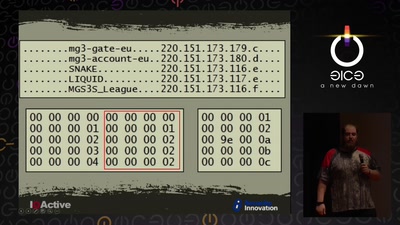
Cyber Necromancy
Reverse Engineering Dead Protocols
48 min
10 Years of Fun with Embedded Devices
How OpenWrt evolved from a WRT54G firmware to an universal…

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
60 min
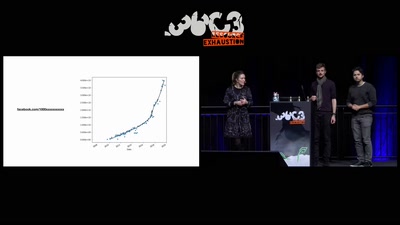
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…
60 min
The Perl Jam 2
The Camel Strikes Back

43 min
Sanitizing PCAPs
Fun and games until someone uses IPv6 or TCP

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

69 min